String Encryption
Encrypts all string literals in your code to prevent easy extraction of sensitive text and make reverse engineering significantly harder.
 LedgerFuscator
LedgerFuscator
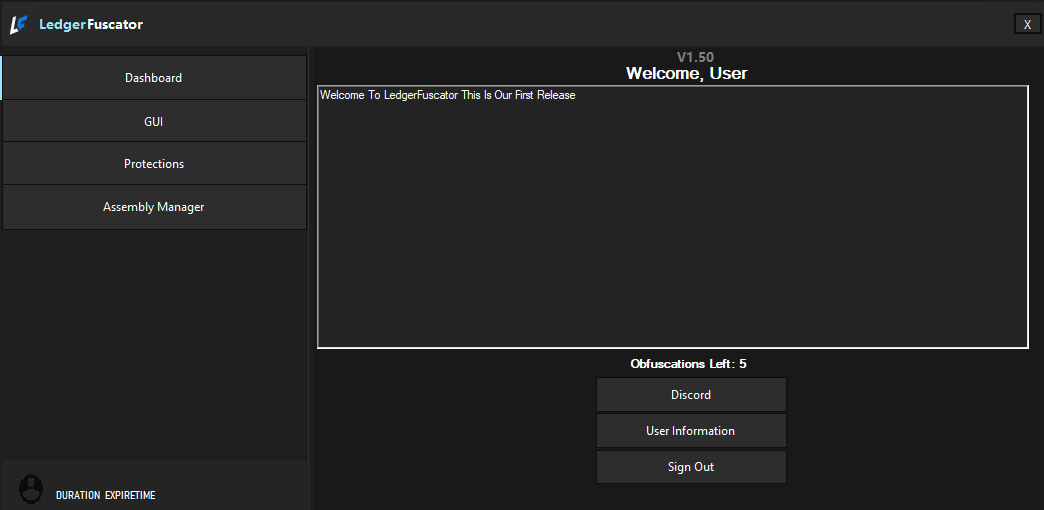
Everything a Developer needs — securely and transparently.
Encrypts all string literals in your code to prevent easy extraction of sensitive text and make reverse engineering significantly harder.
Flattens and obfuscates control flow structures to confuse static analysis tools and make code execution paths difficult to follow.
Makes The Program Run Virtually Making It Almost Impossible To Reverse Engineer
Obfuscates stack operations and local variables to prevent analysis of method internals and data flow.
Intentionally slows down dnSpy and other decompilers by adding complex structures that cause performance issues during analysis.
Inserts conditional statements that always evaluate to the same result, confusing static analysis and making code flow harder to determine.
Replaces direct string access with proxy methods that decrypt strings at runtime, making static string extraction impossible.
Specifically targets dnSpy decompiler with anti-analysis techniques to prevent successful decompilation of your protected code.
Converts local variables to instance fields, making code analysis more difficult by changing the variable scope and access patterns.
Inserts dummy method calls that appear functional but serve no purpose, confusing reverse engineers about actual program behavior.
Encapsulates field access through properties or methods, adding an extra layer of indirection that complicates analysis.
Protects against de4dot deobfuscator by implementing techniques that prevent successful deobfuscation attempts.
Modifies assembly metadata and attributes to mislead analysis tools about the actual structure and origin of the code.
Adds misleading custom attributes to classes and methods, confusing analysis tools about the actual purpose of code elements.
Renames and restructures methods to make them unrecognizable while maintaining functionality, preventing easy identification.
Replaces simple arithmetic operations with complex equivalent expressions, making mathematical operations harder to understand.
Inserts code that appears valid but is never executed, creating false paths that waste time during reverse engineering.
Injects meaningless code blocks that execute but produce no useful results, cluttering the decompiled output and wasting analyst time.
Wraps method calls through proxy functions that add indirection layers, making it harder to trace actual method execution.
Automatically renames classes, interfaces, and namespaces to meaningless identifiers, making code structure unrecognizable.
Detects and prevents analysis by common malware analysis tools and sandbox environments to protect your obfuscated code.
Detects virtual machine environments and can modify behavior or prevent execution to avoid analysis in sandboxed environments.
Modifies the Portable Executable header to mislead analysis tools about file properties, compilation date, and other metadata.
Simple pricing for teams of any size. All plans include free trials and enterprise onboarding.
Ethics & Legal: LedgerFuscator is intended for a shield for your .NET Assemblys Not To Abused To Hide Malicious Code